We think that connecting to a website over HTTPS is secure, which is true(not true sometimes!), but what about DNS queries that you(browser) send?
Sure if we use HTTPS, all your (POST or GET) data is encrypted end-to-end which prevents eavesdropping, MITM attack and have Confidentiality, but again what about DNS queries?
I got this question back a while ago, so after a quick Internet search, I found DNSCrypt protocol which is cool because I can encrypt DNS queries.
First of all, what the heck is DNS? in simple, DNS or Domain Name System is a service that resolves/translates domain “name” to “IP” or vice versa. So once you hit google.com in your browser, a DNS query fired to DNS host(for example 8.8.8.8) like asking “what is the IP of google.com” and gets DNS responses which contain IP of google.com. Now we got the IP of google.com, and the browser initiates a connection and establishes HTTPS.
So, you see these DNS queries are not part of “HTTPS”. So let’s encrypt DNS queries with DNCrypt.
Why should we care about “DNS queries encryption”? Well, sometimes eavesdroppers are interested in the metadata of communication rather than actual communication.
What is DNSCrypt?
DNSCrypt is a protocol that authenticates communications between a DNS client and a DNS resolver. It prevents DNS spoofing. It uses cryptographic signatures to verify that responses originate from the chosen DNS resolver and haven’t been tampered with.
It is an open specification, with free and open source reference implementations, and it is not affiliated with any company nor organisation.
There are some points to be noted
- In order to use this protocol, we should install a package called dnscrypt-proxy
- Normal name servers(like 8.8.8.8) won’t support this protocol. We should use these DNS resolvers
dnscrypt-proxyby default binds on loopback interface (127.0.0.1) 53 port. So, I have to change the title configuration.
Install dnscrypt-proxy
From Ubuntu 16/ Linux Mint 18.x, dnscrypt-proxy is available in the official repo.
sudo apt-get install dnscrypt-proxy
I found a PPA for Ubuntu 14.04 and Linux Mint 17.x
sudo add-apt-repository ppa:anton+/dnscrypt
sudo apt-get update
sudo apt-get install dnscrypt-proxy
Start dnscrypt-proxy
After installation, with --help argument get options and run accordingly. But luckily I created a python script which will do it for you.
wget -qO dnscrypt.py https://goo.gl/zjZYVR
sudo python dnscrypt.py
After you run the script, it will list the DNS resolver details like below.(The script downloads resolvers csv and passes this file as argument to `dnscrypt-proxy``)
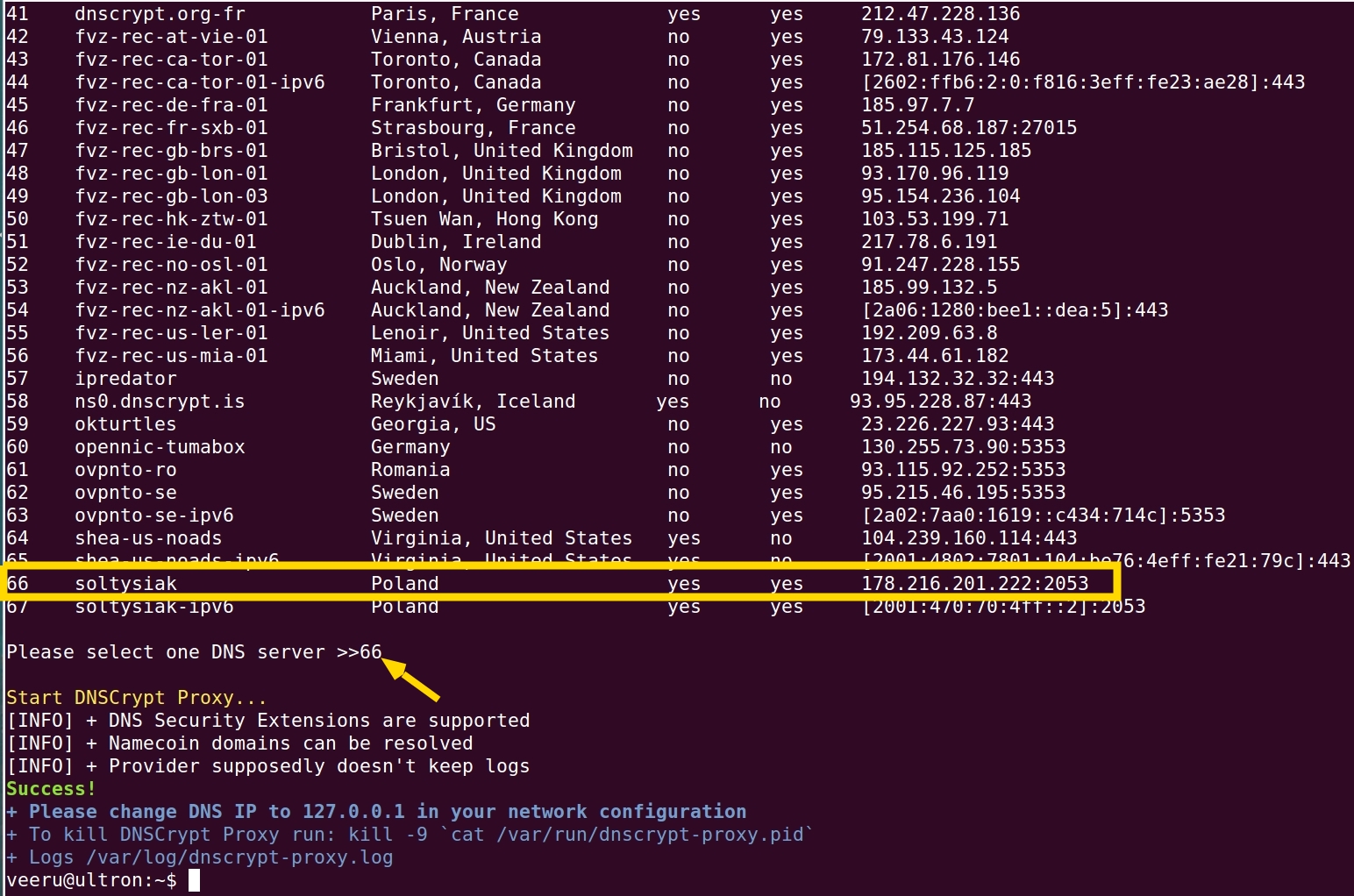
Select one name server. You can see these name servers have options DNSSec & No Logging which provider can log your queries, choose one accordingly (These options/table header you can’t see in the above screenshot. You have to scroll up)
Next, configure your network settings like below
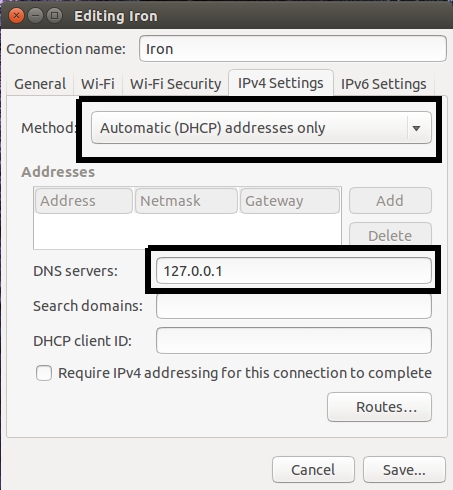
Restart the network (disconnect and connect wifi) and you are done!
To verify run tcpdump -i any -n port 2053 (Why 2053 port? because in the above screenshot I selected the 66 option which has 178.216.201.222:2053)
What’s happening?

Go beyond this script!
I created an init script which runs at system boot. So that there is no need to run the above script again and again.
- Download resolvers csv file with –>
python dsncrypt.py -d - Specify
resolver_name(By default it hassoltysiakwhich hasNo Loggingpolicy andDNSSec) in the script.
sudo wget -O /etc/init.d/encryptdns https://goo.gl/opZ78J
sudo chmod +x /etc/init.d/encryptdns
sudo update-rc.d encryptdns defaults
sudo service encryptdns start
Github Repository Link
DNSCrypt in Windows
Other resources you can try